Under the microscope: Need For Speed: High Stakes & Porsche Unleashed (PlayStation)
Reverse engineering the cheat code obfuscation systems in some PlayStation racing games
In this edition, I’m examining two PlayStation games in the Need For Speed series. I found some previously-undiscovered elements in these games.
For High Stakes, I reverse-engineered the mechanism that the game uses to hide cheat effects from people snooping on the binary. This revealed a long-unknown (and silly) Easter egg.
For Porsche Unleashed, I worked out how the cheat code system works. This revealed two more cheat codes that have stayed secret for more than 25 years.
Details are below!
Need For Speed: High Stakes
As of this writing, GameFAQs lists several cheats for Need For Speed: High Stakes:
Select the User Name option at the game option screen and enter the following:
Cop Code: NFS_PD
Fly Police Helicopter: WHIRLY
Phantom: FLASH
Titan: HOTROD
Indeed, these do work. But how? If you search the game’s data for any of these strings, you won’t find them.
I entered a name at the prompt and then took a snapshot of my emulator’s memory. Then I searched for my name. It came up in plaintext:
80115c1c "32bits"Then I set a read breakpoint for that address to see what the game does with that input after it’s entered.
The function at 80023634 trips the read breakpoint. It does this:
Applies a transformation to the name you entered.
Compares the transformed value to three static ones.
If there’s a match, sets one of the bits in the field starting at
8013e550.
The transformation function is not a cryptographically secure hash by any stretch. Here’s a Python version of it:
def transform_01(data):
return bytes(
sum(((data[y] >> x) & 1) << y for y in range(8)) for x in range(8)
)This function is its own inverse, so to get plaintext version of the three static values, we can just apply it to the scrambled values:
0c090312081e1f00 -> "Flash"
121a36130c3e3f00 -> "Hotrod"
25091136293e3f00 -> "Whirly"Those match the special names from above – no surprises. What about the fourth one?
The function at 80023800 also trips the read breakpoint. It uses the same logic as above, but it (a) uses a different transformation function, and (b) checks two values instead of three. The transformation function here is a bit more complex, but it’s still not cryptographically secure. My re-implementation of it is here.
The static values decode to:
cd9988d7bfbbbfff -> "Nfs Pd"
87dfdfab9d8fd8ff -> " Yrag"Nfs Pd is the “cop code” from above, but what’s Yrag with three spaces in front of it?
When this name is detected, the game sets the 12th bit on the flag field mentioned above. Looking for references to that flag field’s 12th bit leads to the function at 80036278. I set a breakpoint for that function and then fiddled around until I got a hit.
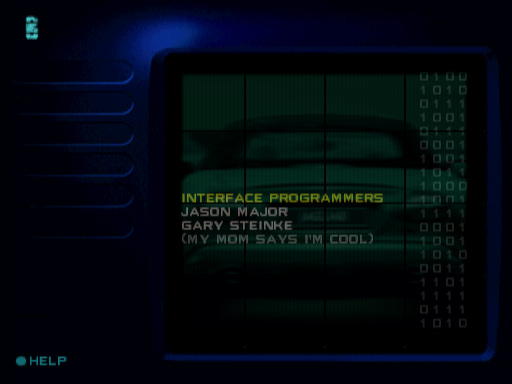
The breakpoint tripped on the Credits screen (go to Game Options > Credits). Normally, you see this:
But if you enter the special name, you see this:
This seems to be the only effect – a goofy Easter egg! Presumably Yrag is meant to be Gary backward.
Need For Speed: Porsche Unleashed
The Cutting Room Floor describes a “Cheat mode” code for this game. You have to:
Select Credits from the main menu.
Enter this sequence: Up, Down, Right, Left, Circle, Square.
Press Triangle to leave the credits.
You’ll see Beta 1.0C on the main menu if you got it right:
Searching for that string in memory leads to this location:
800b3a2c "BETA 1.0C"Tracing references to that string leads to the function at 8003c570, which checks whether the byte at 800bf9dc has a non-zero value. This byte serves as the “cheat mode” flag.
Tracing writes to that flag leads to the function at 800203b0, which is what gets called when you enter the button sequence correctly. That function is referred to by the data structure at 800a87fc, which has this format:
Button code (4 bytes)
Unknown value (4 bytes)
Callback function pointer (4 bytes)
The button codes use the standard PlayStation mapping:
800a87fc 1000 0000 # Up
800a8808 4000 0000 # Down
800a8814 2000 0000 # Right
800a8820 8000 0000 # Left
800a882c 0020 0000 # Square
800a8838 0080 0000 # CircleRight next to the data for the cheat mode code is another block with the same format. Its buttons are:
Right, Left, Right, R2If you enter this on the screen that checks your memory cards (just before the main menu pops up), the string French will appear in the top-right corner of the screen. Enter it again and you’ll see German:
Indeed, the menu language changes after entering the code:
You can get French, German, Spanish, Italian, and Swedish.
There are more codes, too! This one is entered during gameplay (you can do it from the pause screen):
L2+R1, L2+R1, R2+L1, R2+L1, RightYou really have to nail the timing on the shoulder button presses – hit both buttons at the same moment.
Your reward will be three extra cars. Here’s the GT2:
And the 917:
And the 911 GT1:
The callback function for this cheat prints this message to the console (it’s not visible to you as a player):
800a9a50 "ALL CARS DELOCKED !"There are two other cheat codes like this:
ALL GAME MODE DELOCKED !: L2+R1, L2+R1, R2+L1, R2+L1, Left
ALL TRACKS DELOCKED !: L2+R1, L2+R1, R2+L1, R2+L1, Up
However, these don’t actually do anything. The game doesn’t have any unlockable modes or tracks. It’s unclear if it was originally meant to have these features, or if this code is recycled from an earlier game that did. I’d love to know – if you know any of the developers, send them this article and have them get in touch!
Outro
For many more cheat code discovery posts, see my archive here.
More retro game reverse engineering articles are coming soon! Subscribe here on Substack to get them as soon as they come out:










Nice finds! I love the Need For Speed games on the PSX. Good times.I still play them today especially High Stakes.